All in Fieldcraft
Sometimes you don't know what you agree to until it's too late. In this particular project we were testing physical security around the customer's building. The customer asked us to try to bypass their physical security measures and if possible reach a certain room and leave a note there.
It sounded like a fun project.
The next 3 weeks were spent researching the target, recon during the day and night, trying to get the right names for some social engineering attack if needed and gear, techniques and planning.
At the end we discovered a vulnerability and we thought we could exploit to get us in. The only problem was that in order to get that potential point of entry we needed to get to the roof.
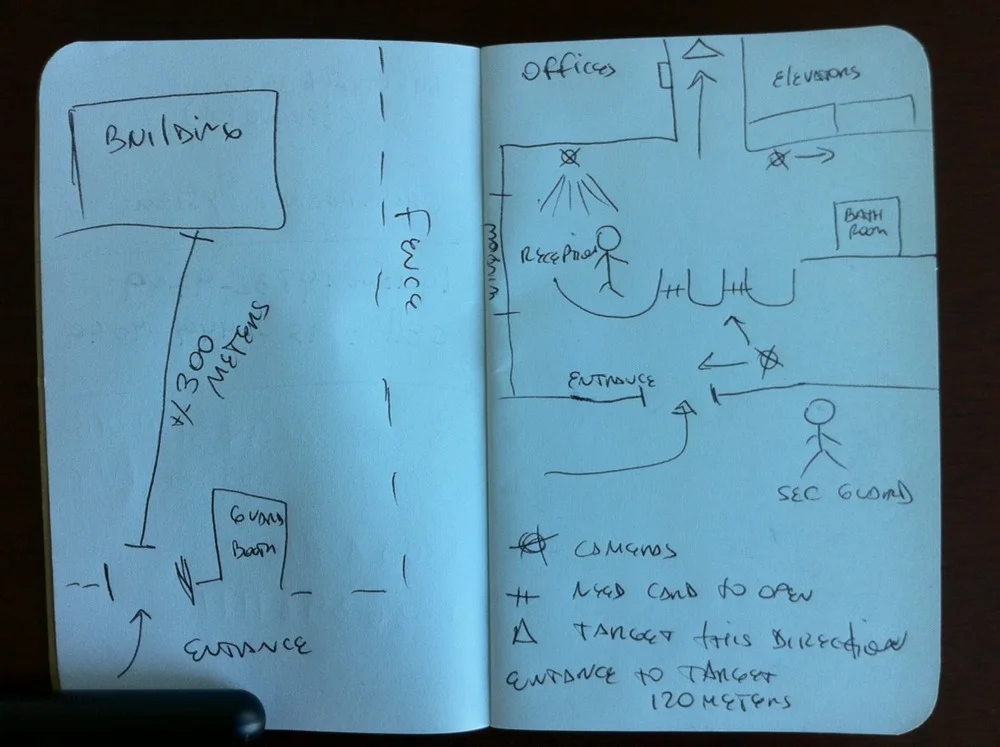
Casing a site
I had this post set to appear in a few weeks as a response to the different readers sending their questions after a few posts about recon and site casing, but after the fun post by Jason at GORUCK about this subject, I thought I'd post it now.
Like I mentioned before, recon is crucial to a successful operation, be it physical or digital. A key part of this is the site casing: observing a location and learning its vulnerable points, its atmospherics, its rhythm. Knowing the locations of entrances and exits, potential choke points, security cameras and other devices can influence what you do or don't do. It also help planning the escape routes. Yes: Rule 1 - Always have an escape plan.